same as first exploit use fuzzer, but here we make special fuzzer
to try server chat easy, before our exploit us server chat easy instal xp
xindows, install style hence its result will like hereunder.
Next process , we edit name user and password exist in server chat,
after editing us open URL exist in server chat on condition that we have to
opening linux why we have to open linux because here we wireshak pake, just see
picture.
After
us open hence wireshark appearance will like this.
Step hereinafter double click in existing
wireshark password and name we, will seen result of like this.
and we can look together wireshark catch protocol HTTP and look
the username and password. so copying the header and host in script fuuzzer.
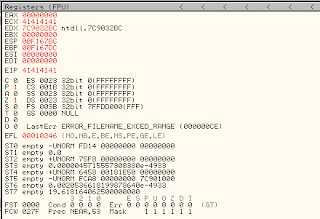
If us have made our fuzzer step into windows and run Ollydbg, when have run hence its result like this.
in Olydbg we can see stack memori.
right click continue to select dumb, here we earn to see address in change memory.
step hereinafter we make fuzzer.
Make pattern as many as possible character to make fuzzer 2, if me make 135000 character. Send fuzzer with python to make accident Easy Chat Serve.
After Easy Chat Serve crash , see in Ollydbg and appearance select;choose SEH chain to see from Easy Chat Server. Depress " shift + F9" which sharpness see picture.
Thereafter we check EIP offset pattern enlist and using to third, see picture.
afterwards we reenter to windows to run Ollydbg unutk look for jumping movement stone.
there after we can look for POP r32, POP r32, RETN we can see its result like this.
After us ascertain Vbajet32.Dll can be used as next stepping point us look for byte to how much in buffer. our berikutya process make fuzzer 4 seeing picture following seeing picture.
Step hereinafter run Easy Chat Server application, last attachkan process Easy Chat Server into Olydbg, last Ollydbg run us, afterwards we run Easy Chat Server application content use pattern. Easy Chat Server will become crash, see picture.
Step hereinafter we make shellcode for the exploit of, same as other that is goals system will open port 4444 its system. Here we use msfweb for the generate of paylod, more clear see picture.
Next us make fuzzer 5 seeing picture
Step hereinafter run Easy Chat Server application, this us not to pass on Ollydbg, afterwards we run fuzzer we which have change with new payload, see picture.
Success.


















Tidak ada komentar:
Posting Komentar