Here we will study the way of linux exploit,
first step which must kill ASLR linux.
We can see picture of way of killing ASLR linux.
Type : root@bt: cat /proc/sys/kernel/randomize_va_space
root@bt: echo
0 > /proc/sys/kernel/randomize_va_space
root@bt: cat
/proc/sys/kernel/randomize_va_space
Second step us make Ianguage pemrograman C++ see picture.
Let us see at the time of us compile.
We can turn the SSP off by adding the “-fno-stack-protector” flag to gcc when compiling.
Let’s open it in GDB and try to find the offset needed to trigger an overwrite. see picture.
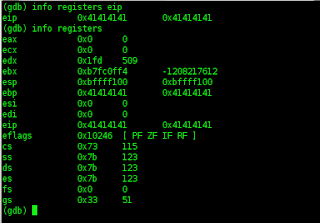
As we can see we have managed to successfully overwrite the EIP
Next step us do register see picture.
So using “info registers” we can see all our registers and with the “x/FTM ADDRESS” we can check out a particular register (in this case ESP).
Next step We would get the address of ESP before the last 200 bytes of our buffer get pushed on the stack.
Next step us check over one ESP address see picture.
Than now we try to genarate payload before that we must have file fore make a payload
After getting payload let us try exploitasi.
Success
Don't have surendered learnt, yes although that is hard.








Tidak ada komentar:
Posting Komentar